Hitting back at hack attacks
Hackers can wreak untold havoc. Take, for example, the 2020 case in which criminals were discovered to have been exploiting issues in a Chinese government website’s facial recognition system to create fake tax invoices over a two-year period worth US$76.2 million. Issues like these happen because of the inevitable vulnerabilities of new software—so two research teams from the Department of Information Engineering are trying to prevent hacks by pinpointing exactly what those vulnerabilities are.
One team, led by Professor Lau Wing-cheong, investigated precisely the sort of software exploited in the example above. Used for everything from opening bank accounts to age verification, facial recognition is supposed to be a foolproof way of guaranteeing security. Unfortunately, though, in many cases, that’s not the case.
It’s easy to steal a photo of someone that could be used for facial recognition purposes, and devices that can perform an attack are available cheaply. As a result, the software generally asks people to perform what’s known as liveness detection—actions like shaking their head or blinking to prove they’re real. However, it turns out that in some cases, it’s surprisingly easy to bypass these checks with only a still photo.
Professor Lau’s team investigated 18 facial recognition software development kits (SDKs), including a number of the market leaders, and found security flaws in 11 of them. They also used an automatic app analyser they created to scan more than 18,000 apps that use the software and found close to 300 of them featured the vulnerability.
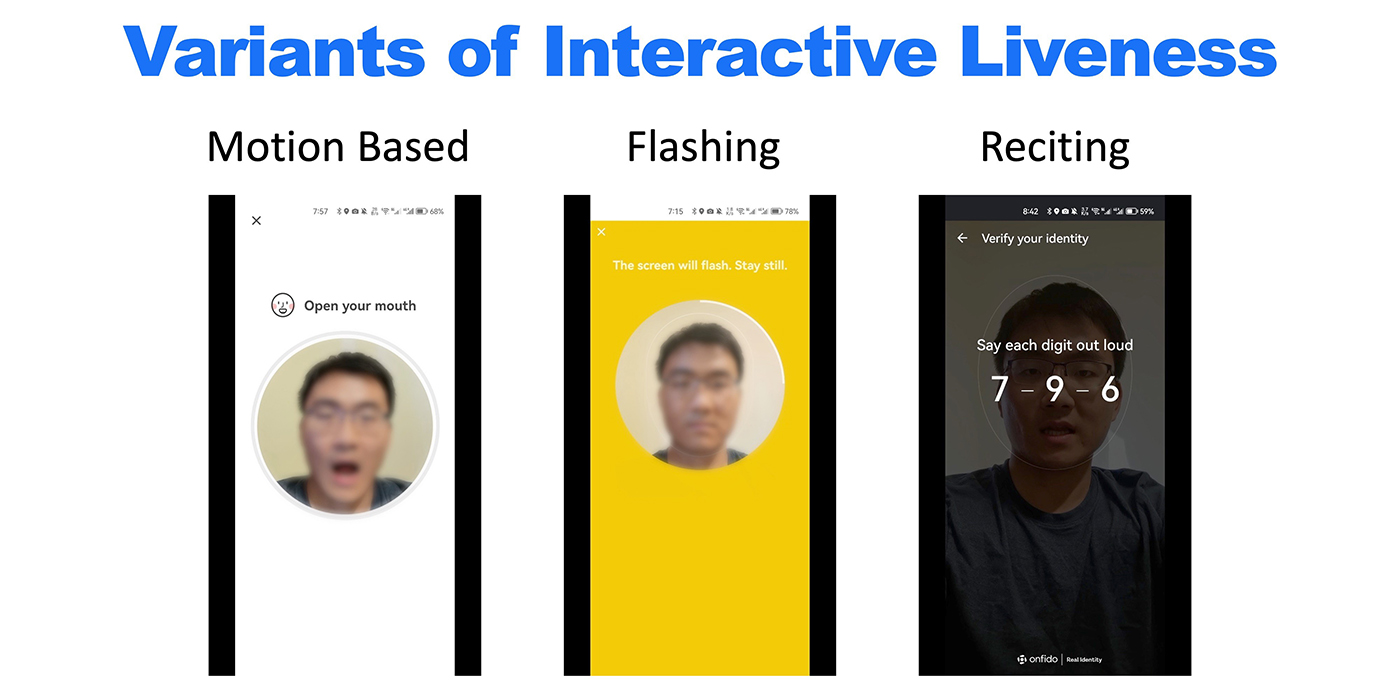
“Several years ago, we saw that the use of this kind of facial recognition technology in mainland China and Hong Kong was growing very fast,” says Professor Lau. “We asked the question: is it really secure? With any new technology, there’s a fundamental limit on how secure it can be.”
“The problem with SDKs is that usually the users are people who own apps. They often outsource development, and the developer will make it work, and that’s it.”
To improve their security, the team’s research paper says, organisations using facial recognition systems should perform cloud-based liveness detection; adopt multiple layers of security control; enforce robust client protection; and properly encrypt configurations and data that are used during the facial recognition process.
The team has alerted the companies to the vulnerabilities. Their reaction has varied widely, Professor Lau says. Some companies are grateful, some don’t even reply, and others are somewhat evasive.
“A lot of the time, after we contact software providers, even if they fix it, they give it a very low-profile treatment and don’t make any explicit announcement. Even after the vendor upgrades the SDK, the app is still vulnerable. As long as the attacker can find an old version of the app still running, people can still be exploited. It is more prudent to mandate users to upgrade their apps when SDK has been updated, just like many banking and finance apps.”
Wi-Fi and VPN setups leave users at risk of password theft
Another research team, led by Professor Chau Sze-yiu, has found similar worrying security issues in enterprises’ Wi-Fi and VPN setups, with users forced to adopt insecure settings. The team studied 7,000 Wi-Fi setup guides from 2,000 universities and other academic institutions, which often make their set-up guides public, and found that 86% instruct users to adopt unsafe Wi-Fi settings, allowing attackers to steal users’ passwords using Wi-Fi impersonators that cost less than US$100 and take less than an hour to configure. Similarly, 63 of the 132 VPN front-end apps they studied have vulnerabilities that allow hackers to steal credentials.
“Most of the time, when people talk about ‘authentication’, they are thinking about user authentication, such as a user logging into a network with username and password. However, in order to prevent an attacker pretending to be the server and stealing the user’s username and password, server authentication is very important. In many appliances, including enterprise Wi-Fi and VPNs, it’s achieved by the client device verifying the server’s certificate. We found that IT admins of many universities did not instruct their users to enforce robust certificate verification.”

Again, the team has informed the institutions affected, with a variety of responses.
“Some academic institutions were very receptive and took immediate actions. Unfortunately, some were not convinced that the security threat is real, and decided to continue with their insecure practices. Quite a number simply did not bother to reply to us. It’s not easy to help people if they don’t want to be helped.”
The team recommends that vendors created products that lead users to choose secure settings; that IT admins educate users how to make systems safe; and that users think carefully about the implications of clicking buttons that say things like “OK”, “Connect” and “Accept”, asking their IT admins for advice if necessary.
“We understand that the convenience of blindly trusting any server certificates is very tempting, but security is not only about making things work, and has a lot to do with making things safe when unexpected exceptions happen,” says Professor Chau.
Reprinted from CUHK in Touch